There’s no question there is a need for endpoint detection and response (EDR). Yet, detection-based EDR tools provide insufficient security. Attackers are smart. They understand how detection-first solutions work, and they continuously develop techniques to slip under everyone’s radar to attack as “Unknowns.” Unknowns cannot be detected. But when you add protection-first, detection-less ZeroDwell Containment to an EDR solution’s front end,
suddenly you experience a paradigm shift and see breaches and ransom incidents plummet without needing to rely on detection.
THE NXL CLIENT SECURITY PROACTIVE ENDPOINT DETECTION AND RESPONSE (EDR)
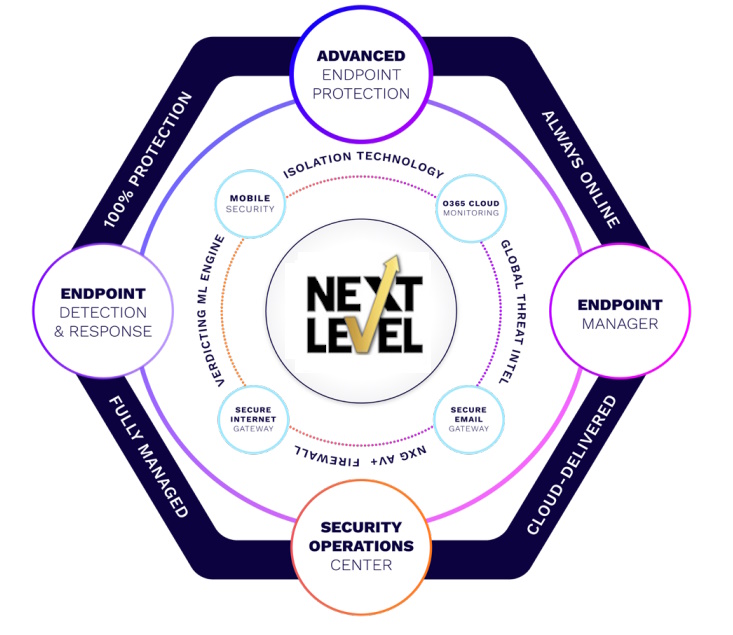
KEY CAPABILITIES
MITRE ATTACK CHAIN MAPPINGS & VISUALIZATIONS
Attack vectors are shown on the dashboard. When combined with file trajectory and process hierarchy visualizations, this accelerates investigations. Process-based events are shown in a tree-view structure to help analysts better understand process behavior.
CONTINUOUS MONITORING | EDR | RECOMMENDED SECURITY POLICY
NXL will create an endpoint security policy, which is customizable to meet individual needs. Our engineering team is available to work with you to tailor security policy to your requirements, especially endpoint-specific policies.
SUSPICIOUS ACTIVITY DETECTION & ALERTING
Get notified about events such as file-less attacks, advanced persistent threats (APTs), and privilege escalation attempts. Analysts can change status of alerts as they take counter-actions to dramatically streamline follow-up efforts. Because of ZeroDwell Containment at runtime, alert fatigue is a thing of the past and you can focus on alerts that matter.
INCIDENT INVESTIGATION
The event search screen allows analysts to run queries to return any detail at base-event-level granularity. Aggregation tables are clickable, letting investigators easily drill down into specific events or devices.
FILELESS MALWARE DETECTION
Not all malware is made equal. Some malware does not need you to execute a file when it is built in to the endpoint’s memory-based architecture such as RAM. Xcitium EDR can detect against this threat before it appears.
PROACTIVE ZERODWELL CONTAINMENT
Unknown executables and other files that request runtime privileges are automatically run in Xcitium’s patented ZeroDwell container that does not have access to the host system’s resources or user data. ZeroDwell Containment means malware cannot move laterally across your network or organization.